IT Support Department Members Explain the "Cloud-Based Web Isolation System" Security Solution that Prevented 20,000 Attempts to Access Potentially Risky Content in One Month
[Notice] Effective October 1, 2023, LINE Fukuoka has changed its company name to LY Communications. Articles published on or before September 30, 2023 were written with our former company name.
This is the IT Support Department's Infrastructure Team.
LINE Fukuoka's IT Support Department handles all in-house IT work, and is made up of five teams: the Help Desk Team, the Help Management Team, the Technical Support Team, the Infrastructure Team, and the Information Security Team. The Infrastructure Team is responsible for office infrastructure operations and network security, and takes on a variety of projects to bolster the company's cyber-security.
In this post, we will explain the details of how the "Cloud-based Web Isolation Service" (a security solution that has prevented over 20,000 major security risks in just one month) came to be adopted, the results it achieved, and some issues surrounding it.
If you're in IT and are searching for a security solution that is effective for in-office as well as work-from-home (WFH) setups, this article is for you!
Making access to websites safer
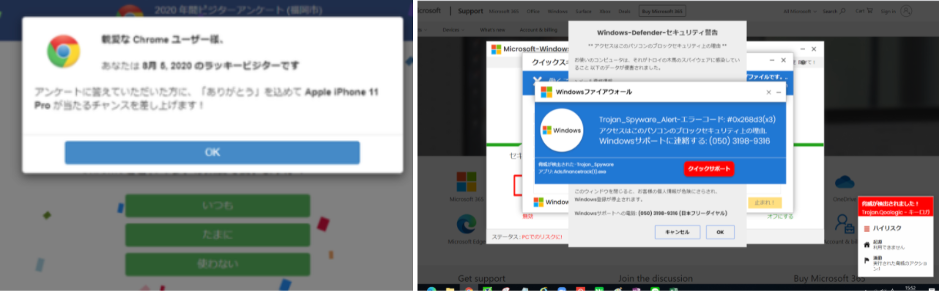
Have you ever unintentionally clicked on a link to a suspicious site when you were just trying to look something up for work? If you connect to a website that targets a weakness in your network or may infect your device with malware, you have to stop working, disconnect from the company network, have your device scanned for viruses, and wait for a cause to be found and dealt with until everything is determined to be safe. These investigations and adjustments also place a burden on internal IT.
Just because you accessed a suspicious site doesn't mean that your PC will be impacted, but obviously, you want to reduce security risks as much as possible, especially on devices like PCs that you use for work.
LINE Fukuoka is responsible for checking if there are any issues with URLs posted on LINE services or in the services handled by companies that have applied for a review of their LINE services (such as their LINE official account). The company was considering a solution that would allow employees to safely access any website, and posed no risk to servers or devices connected to the company's network.
Primary methods of utilizing "web isolation" as a security measure
In simple terms, web isolation is the process of separating web content on a standard internet connection from an internal network. The phrase "internet isolation" is sometimes used in a broader sense, but in this post, you can think of it as one example of a basic security solution. The four primary methods of web isolation are explained below, but after considering costs, usability, and management, LINE Fukuoka chose option 4, "cloud-based web isolation."
Results of introducing a "Web Isolation System"
The graph below shows the number of attempts people using web isolation made to access sites that pose security threats (in the most recent one-month period). We also found history of connecting to malicious content such as malware, and if we weren't using web isolation, those devices may have been infected.
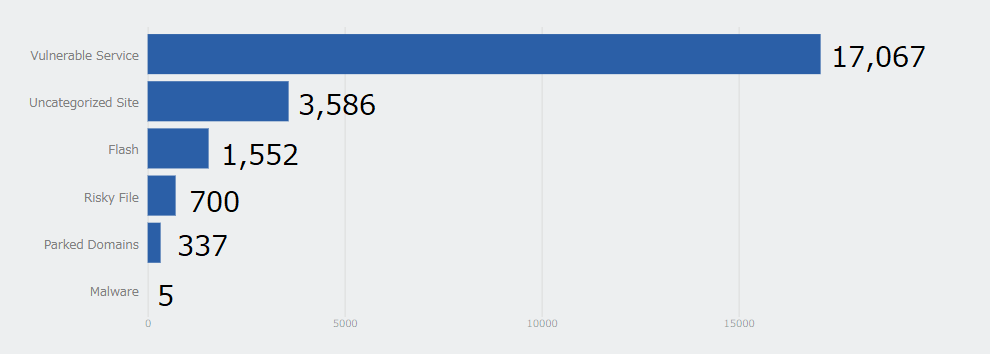
By introducing isolation, we were able to prevent over 20,000 major risks in just one month.
Additionally, there were five confirmed connections to websites that contained malicious content classified as malware. If web isolation were not in place, we would have had to stop working and use man-hours to do investigations, so being able to connect safely allows us to reduce those man-hours.
Perceived issues in introducing a "cloud-based web isolation system"
Cloud-based web isolation systems are extremely effective as a security measure, but in the process of integrating a solution, we also saw some issues.
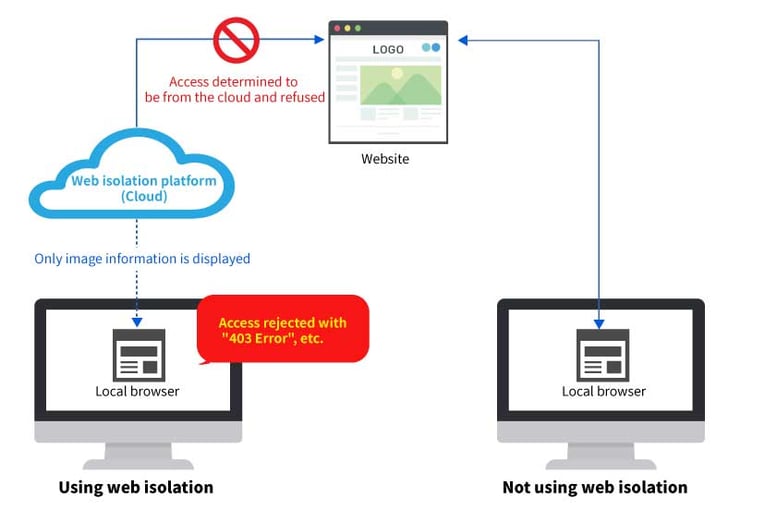
Issue 1: If the connection is controlled by the website, a proper connection may not be established
A website can detect that access is occurring from the cloud because connections to the site take place through an isolated web environment. Cloud access may be blocked depending on the website, so in some cases, sites that were previously accessible can no longer be accessed.
If the website you can no longer access is actually a cloud service being used as part of an in-house system, you can utilize transmission routes such as a PAC to avoid using web isolation. However, adjusting transmission routes so that they don't go through web isolation for normal public websites increases security risks, which is not ideal.
It's also difficult to contact website administrators and request cloud access to their site.
Issue 2: Web isolation can't be applied at the OS level
Originally, we would have preferred to apply web isolation at the OS level and protect all communication from work devices.
If you want to apply web isolation to an HTTPS-encoded website, you need to import a specific certificate authority (CA) for decrypting the secure socket layer (SSL) and transport layer security (TLS) on the cloud to your OS and verify ("trust") it.
However, trusted CAs may be managed independently by applications, so the CA you've imported to your OS may not be trusted. If this happens, SSL/TLS will not function properly because the application can't verify the certificate chain, and your devices will not be able to communicate.
This is why we've currently applied web isolation only for communication from browsers.
Issue 3: The connecting country may not always match the global IP address
Even if your transmission originates from within Japan, it is connected to the region with the lowest latency, so you may not be using a web isolated environment in Japan. If you're connected to a region outside of Japan, you'll no longer be able to use Japan's global IP address, which means that you won't be able to access websites that reject access from other countries.
Also, even if access from outside of Japan is allowed, the page may be displayed in another language.
Issue 4: Websites may not appear properly, but end-users won't be able to notice
Websites that have had malicious content neutralized may not appear correctly, but users won't be able to tell if that's how the site normally looks or if it's due to the effects of neutralization.
For example, information that is displayed incorrectly can have a negative impact on review work, which involves checking the advertisements or videos posted on a site.
Issue 5: It may take a time to connect to a website
With web isolation, websites are displayed after they have been neutralized. This neutralization process starts loading when you connect to a site, and it may take a few seconds for the site to be displayed. On sites with a lot of content, it may take even longer.
For work that requires connecting to several hundred websites, these few seconds can accumulate and cause time to be wasted. Because web isolation isn't the best fit for work that requires accessing a large number of websites quickly, we only integrated the web isolation system into departments that require it.
We'll continue giving our best to ensure that we can solve issues like the ones above. If you read this post and think you may have the information to solve issues like these, you want to introduce a similar system, or you want to hear more details, please feel free to send us a message or leave a comment! The IT Support Department looks forward to exchanging ideas with you.
▼ Inquiry Form
https://linecorp.com/inquiry/linefukuoka/form.html
If you have any messages or comments for us, you can also send them to Mr. Takashi Kaida's (the Enterprise IT Center Vice-Center Head/IT Support Department Head) Twitter account! On Twitter, Mr. Kaida shares Digital Transformation (DX) and information about internal IT information as well as IT recruitment events✨
Related Articles
Learning the Secrets of "1-on-1s" to Achieve Improved Productivity and Teamwork, Even When Working From Home!
Customer Success Planning Department's Mr. Kato Takes the Stage at LINE AI Company All Hands Meeting

Escape KPI Management traps! What is the Review & Sales Department’s monolith project?